How Can Cybersecurity Communication Save Your Organization?
Cybersecurity communication is vital. It doesn’t matter whether you think your security is compromised or not. We’ve got some info that will help you right now.

.avif)
Audit Your Internal Communications
Strategy is an important component of internal communications. Ensure you’re communicating through the right channels at the right frequency with our Internal Communications Channel Audit worksheet.
Access Now →Data breaches, malware attacks, and phishing scams can cripple a business, causing financial losses, reputational damage, and even legal repercussions.
There’s lots of research on the subject, all of which warns that every organization on the planet is at risk. We know this, and you need to realize that your organization might be at risk.
However, you also need to know that there's a powerful weapon in the fight against cybercrime. This is effective cybersecurity communication that operates in the cloud. We’re here to help you find out more about the problem and how to tackle it successfully with proven solutions.
What Research Tells Us About the Cybersecurity Issues
There is an enormous amount of research about cybersecurity issues including effective communication that can help and security measures organizations can take.
The latest IBM Data Breach Report reveals that an alarming 95% of organizations experienced more than one data breach during 2023. It also states that the cost of data breaches globally reached $4.45 million in 2023 — an increase of 15% in three years and an all-time high.
According to the Verizon 2023 Data Breach Investigations Report, the total number of ransomware attacks was 24%, almost double those experienced in 2021. But what is even more concerning to many organizations is that they found 74% of all breaches include a human element. This includes errors, privilege misuse, and the use of stolen credentials, or social engineering. Additionally, they found that 95% of breaches are financially driven, and 83% involve so-called “external actors” from outside the organization.

The Veritas 2023 global report on Data Risk Management: The State of the Market - Cyber to Compliance states that data security, at 46%, is the greatest standout risk that organizations face. This includes data theft, data loss, and ransomware. Furthermore, data security is under constant threat with 65% of respondents admitting they have experienced successful ransomware attacks in the past two years after attackers gained access to their systems. This report also shows that while organizations recognize that risk levels are escalating, they don’t necessarily recognize the risks they face. Only 52% consider their organizations to be at risk, but when presented with individual risk factors, 97% admitted their organizations are at risk.
What is Cybersecurity Communication?
First of all, it’s important to understand what cybersecurity communication is all about.
Imagine a bank heist. But instead of money, hackers are after your company's data. That's where cybersecurity communication comes in. It's like a shield set up to protect sensitive data of your organization by empowering employees and fostering a culture of security. But how does it work?
By clearly explaining cyber threats and what everyone can do to fight them. Regular reminders, training sessions, and even fun campaigns can turn employees into cybersecurity heroes. The key is clear, consistent communication. It's quite simply the difference between being wide open to attack or having a well-informed defense team ready to stop hackers in their tracks.
Free Internal Comms Audit Template to Improve Engagement
Upgrade your company’s internal comms to enhance employee communication
Download Free
Why is Communication Important in Cybersecurity?
In a nutshell, clear effective communication in cybersecurity is vital because it educates employees on best practices to prevent attacks. It also fosters a culture of collaboration and enables swift response during incidents, minimizing damage.
Here's how clear and consistent communication can be your organization's shield against cyber threats:
Empowering Employees
Many cyberattacks exploit human error. As Verizon’s report reveals, 74% of all breaches include the human element. By educating employees about email cybersecurity best practices including strong password hygiene, identifying phishing attempts, and reporting suspicious activity, you immediately create a human firewall. Regular communication through training sessions, email reminders, and even posters can significantly improve employee awareness.
To reinforce these efforts, a proper DMARC setup adds a technical layer of protection by preventing domain spoofing and ensuring only authorized senders can use your domain.
Enhancing Response and Recovery
Communication is crucial during a cyberattack. Having a comprehensive cybersecurity policy and a clear incident response plan and communicating it effectively to employees minimizes confusion. It also ensures everyone knows their role in containing the damage. Regularly testing the plan through simulations helps identify communication gaps beforehand.
But one issue that many organizations fail to address is that unless they are using an external cloud-based system, when they’re under cyber attack, they’re not going to be able to communicate via email.
Gaining Leadership Buy-In
Cybersecurity needs resources. Clear communication with leadership can help them understand the financial and reputational risks of cyberattacks. Framing cybersecurity, not just as a cost, but as an investment that protects the organization's future, can garner necessary support for security measures.

Best Practices for Effective Cybersecurity Communication
The Cybersixgill Cybersecurity in 2024 report focuses heavily on risks associated with AI. But ultimately it states that there is a need to safeguard existing infrastructure by minimizing risks and to seize new opportunities. They acknowledge that it’s tricky. Certainly, there is no doubt that effective communication is paramount, but what else can you do?
”There is one certainty in cybersecurity — there will be more breaches, and the costs will continue to climb. We are at the cusp of multiple societal, economic, and technological innovations changing life as we know it, further blending our physical and digital lives.”
Cybersixgill
Let's look at what organizations can do before, during, and after experiencing a cybersecurity attack. Every part of the experience will be stressful for many people, so do what you can to mitigate the experience.
Free Internal Comms Audit Template to Improve Engagement
Upgrade your company’s internal comms to enhance employee communication

Download Free
Before and After a Cybersecurity Attack
Develop pre-configured communication templates
Having pre-drafted communication templates allows for faster response. These templates can be for internal announcements, phishing warnings, or updates for clients. All of these need to be customizable for the specific situation to make it easier for leadership to respond quickly and efficiently.
Tailor the message
Use language that your audience understands. Technical jargon might go over employees' heads, while overly simplistic explanations might not resonate with leadership. Try to get it right!
Focus on benefits
Highlight how cybersecurity protects the organization, its employees, and its customers. Frame it as a way to maintain a competitive edge.
Use multiple channels
Communicate through emails, training sessions, internal newsletters, and even social media for awareness campaigns.
Make it engaging
Ditch dry lectures. Use real-world examples, interactive training sessions, and even gamification to keep employees engaged.
Regularly reinforce the message
Cybersecurity awareness shouldn't be a one-time event. Integrate it into your company culture through ongoing communication.

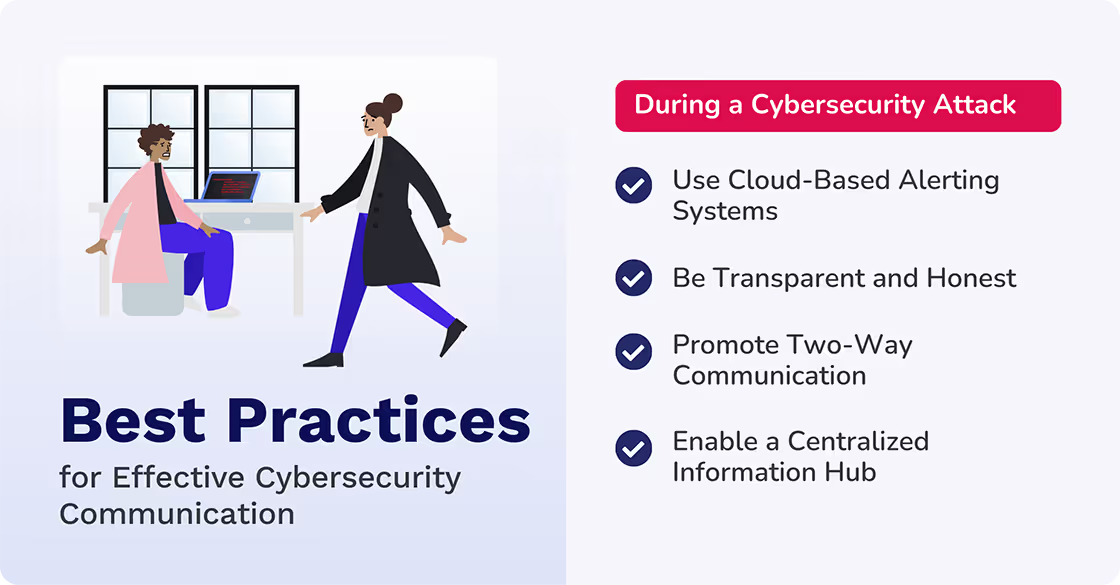
During a Cybersecurity Attack
Use cloud-based alerting systems
Utilize cloud-based notification systems to send out immediate alerts to affected individuals. Cloud services often have built-in notification features or integrate with other communication software for swift and wide dissemination of critical updates. They work!
Be transparent and honest
Be upfront with employees, customers, and partners about an attack. Explain the nature of the breach, the potential impact, and the steps you're taking to mitigate the damage. Cloud providers often offer communication tools and templates to help craft clear messages.
Promote two-way communication
Two-way communication during cyberattacks ensures everyone stays informed and can contribute to a swift, coordinated response.
Mark Oldham, technical manager of YorCyberSec is dedicated to improving cybersecurity. His message makes 100% sense.
Effective communication with customers and key stakeholders during a cybersecurity incident involves actively monitoring and responding to feedback. Listening to their concerns, questions, and comments is a good idea, and addressing them in a timely, respectful manner is key. Expressing gratitude for their patience and asking for their input on improving communication and services helps build trust. This feedback is valuable for identifying any missteps in your messaging and for shaping your recovery and prevention strategies.”
Mark Oldham
Enable a centralized information hub
Create a secure, cloud-based information hub where employees can access the latest updates, FAQs, and resources related to the attack. This reduces confusion and ensures everyone has access to accurate information. Many intranet tools offer functionalities perfect for creating such a hub.
Mila Araujo is a personal cyber insurance practice leader for AVP DIgital SHield in the U.S. and Canada. This is her advice for organizations.
“It’s a good idea to prepare an FAQ to be ready to share with impacted individuals so that they have some additional resources to find more information. Update the FAQ as questions start to come in and use this as a source of information to help fine tune additional communications or resources that you may want to create to help your customers or impacted individuals get through the incident.”
Mila Araujo
How to Keep Your Comms Live During a Cyberattack?
Having a cloud-based internal communication system is crucial if your organization finds itself under cyber attack. With Cerkl Broadcast you are able to communicate with your employees if there is a ransomware attack or a shutdown of your system. Since Broadcast is outside of your system - in the cloud - you can still reach employees via the mobile app or email. If you can’t communicate with your employees at a time like this, it’s like throwing gasoline on the flames of a small fire. It empowers the attackers, leaving your organization defenseless.
Broadcast runs on Google Cloud, the industry’s most secure cloud provider. We take security seriously, so much so we’ve been given Google Cloud Partner status. In addition to the security provided through being in the Google Cloud, Cerkl has also received a SOC2 attestation, offering protection of system resources against unauthorized access. This demonstrates our commitment to protecting customer data and information.
Access controls help prevent potential system abuse, theft or unauthorized removal of data, misuse of software, and improper alteration or disclosure of information.
Crucially, because our system operates independently of every company's internal systems it ensures that customer communication channels remain functional even if their internal systems are compromised. You can remain assured that your company’s core communication methods are protected from security breaches at all times.
What’s Next?
A good start is to read more about our security standards. Then, learn how to map and use your company wide channels and mediums as part of your comprehensive cybersecurity policy.
Be aware that simply having your app installed is a false line of reasoning. Your focus needs to be on email comms during a cyber attack. Cerkl is here to help you all the way. Our system is cloud-based and you will always be able to communicate via email.

Free Internal Comms Audit Template to Improve Engagement
Upgrade your company’s internal comms to enhance employee communication
Download Free
FAQ
What is cybersecurity communication? Cybersecurity communication involves clearly explaining security protocols and threats to employees. It is vitally important to foster a culture of awareness, and ensure everyone understands their role in protecting the organization's data at all times.
Why is it important to have a comprehensive cybersecurity policy? A comprehensive cybersecurity policy outlines clear expectations for employee behavior online. It establishes effective communication that includes incident reporting procedures and helps organizations respond to attacks more effectively by guiding decision-making and minimizing confusion. Without a comprehensive cybersecurity policy, organizations would be vulnerable to confusion, wasted time, and potentially severe data breaches during an attack.
What are the best practices to communicate during cyberattack? During a cyberattack, transparent effective communication is key. It’s vital to keep employees informed about the situation, what actions are being taken, and any precautions they need to take. Be honest, but avoid creating panic and provide updates as the situation evolves.









